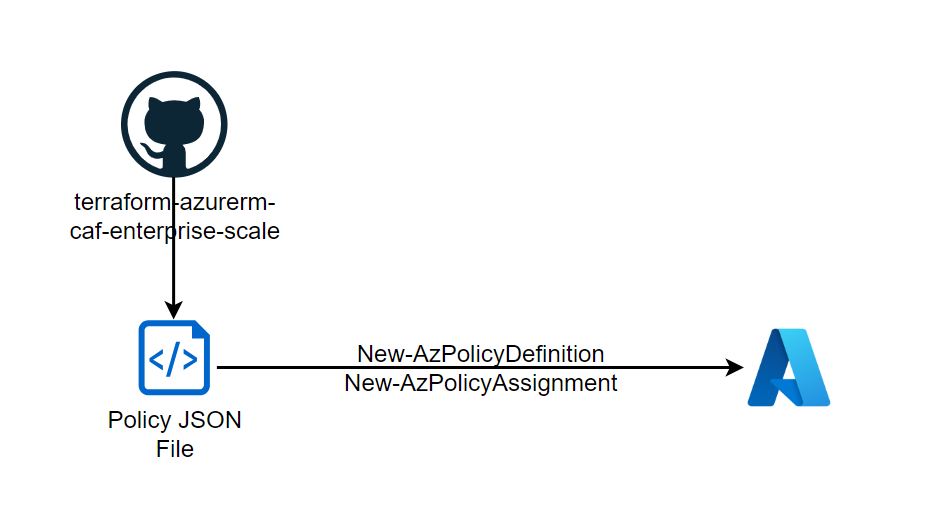
With the Enterprise Scale Architecture, Microsoft offers various landing zone designs that can be used directly as Terraform or Bicep. Interesting is that the repository also contains policies that are not available in the Azure portal. Microsoft recommends these policies for Azure Landing Zones and regularly provides them with updates and develops additional ones.
It is therefore very practical to use these policies directly and provision them in your own environment. To do this, the policy (here policy_definition_es_deploy_diagnostics_acr) is saved locally in line 1 with Invoke-WebRequest and defined in its own tenant with New-AzPolicyDefinition (line 3). The assignment (here to the resource group rg-acr) can then be made to a scope (management group, subscription, resource group) with New-AzPolicyAssignment. An identity may need to be created or referenced using IdentityType if the policy needs to manipulate resources. In addition, any required parameters must be defined beforehand (line 4) and passed on during the assignment.
$resp = Invoke-WebRequest "https://raw.githubusercontent.com/Azure/terraform-azurerm-caf-enterprise-scale/main/modules/archetypes/lib/policy_definitions/policy_definition_es_deploy_diagnostics_acr.json"
$plcy = $resp.Content
$plcyDef = New-AzPolicyDefinition -Name ($plcy | ConvertFrom-Json).Name -Policy $plcy
$param = '{"logAnalytics" : { "value" : "/subscriptions/<SUBSCRIPTION ID>/resourceGroups/rg-log/providers/Microsoft.OperationalInsights/workspaces/la-network"}}'
New-AzPolicyAssignment -Name $plcyDef.Name -PolicyDefinition $plcyDef -Scope "/subscriptions/<SUBSCRIOTION ID>/resourceGroups/rg-acr" -PolicyParameter $param -IdentityType 'SystemAssigned' -Location 'westeurope'
The enterprise scale repositories are constantly being developed. It is always recommended to follow these recommendations or adopt best practices and implementations.
1 Pingback