Schlagwort Application Gateway
The Azure Application Gateway supports various routing options. With path-based routing, one or the other backend can be called depending on the URL. Things get a little more complicated when the apps on the app services are distributed in virtual… Weiterlesen →
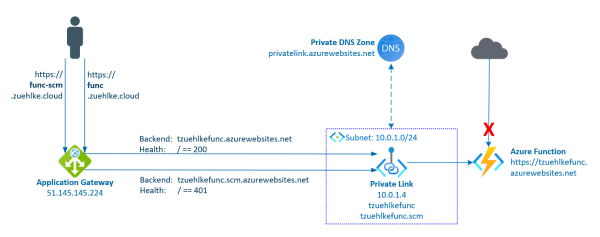
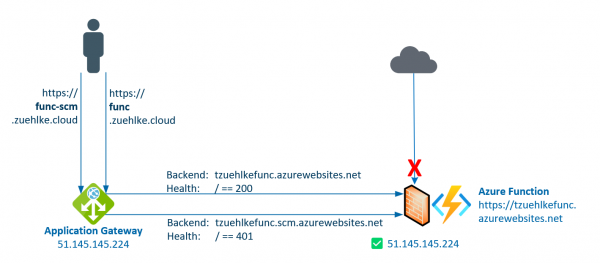
The previous post described how to deploy to an Azure Function if access is protected by an Application Gateway. Access to the function and to the management endpoint as well were protected. The Function was protected by the Function App… Weiterlesen →
Azure Functions are a serverless way to run code. They support different programming languages and can scale quickly. As a developer, it is particularly easy to deploy functions directly from Visual Studio or Visual Studio Code. Functions are often protected… Weiterlesen →
Most resources in Azure can be well protected by disabling public access. If public access is completely deactivated, access can take place via private endpoints. In most cases it is sufficient to restrict access to selected network to use service… Weiterlesen →
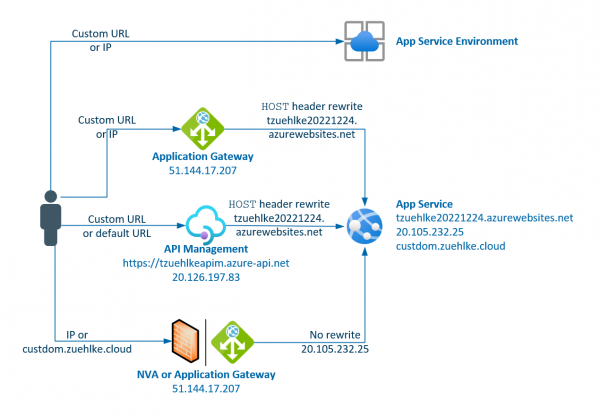
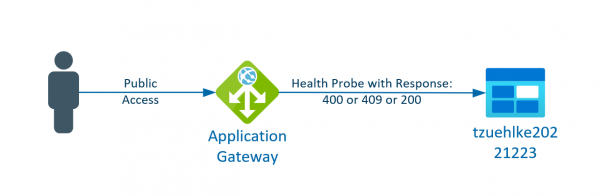
If an AppService is called directly via its IP, either the certificate is invalid or the page cannot be found. If the call is made via HTTPS, the automatic generated certificate only stores the DNS name and not the IP,… Weiterlesen →
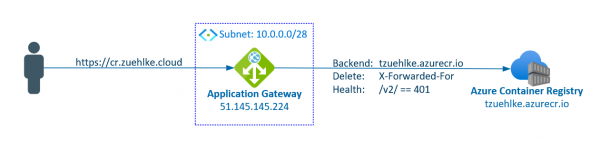
Storage accounts are also often used as backend pools for Application Gateway. This allows the storage to be protected with private endpoints or service endpoints and accessed via a central entry point with an alternative URL. However, the Application Gateway… Weiterlesen →
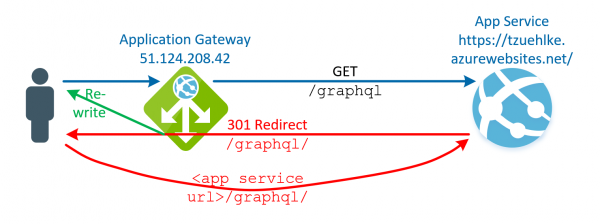
Azure App Services are often placed behind an Application Gateway. Routing is easier to control, your own certificates can be stored centrally and data traffic can be checked and attacks detected. However, if the App Service responds with redirects, the… Weiterlesen →
The Application Gateway v2 has considerable advantages over the v1. Support for autoscaling, zone redundant operation or use as an ingress in the AKS are just a few features from the list. The re-encryption of the back-end data traffic is… Weiterlesen →
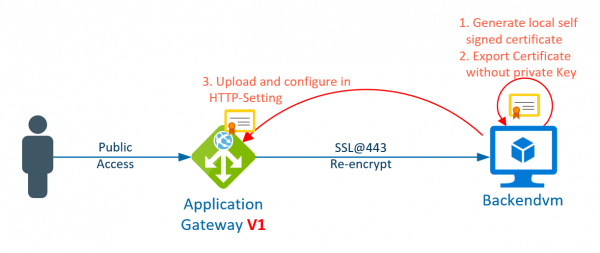
The Azure Application Gateway is a load balancer with some additional features, such as path-based routing, a web application firewall or SSL termination. However, if the traffic to the backend has to be encrypted also, (it has to be re-encrypted),… Weiterlesen →
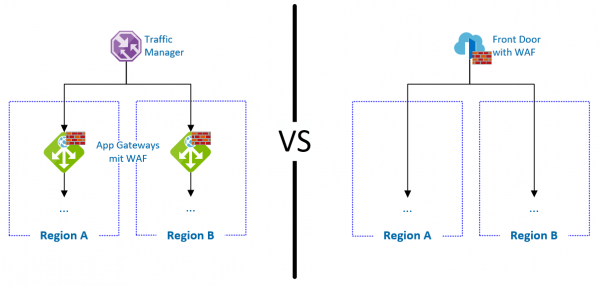
There is often a requirement that workload be distributed across multiple Azure regions. If these are services that are publicly accessible from the Internet, the use of a firewall is recommended. The standard setup was usually the combination of a… Weiterlesen →