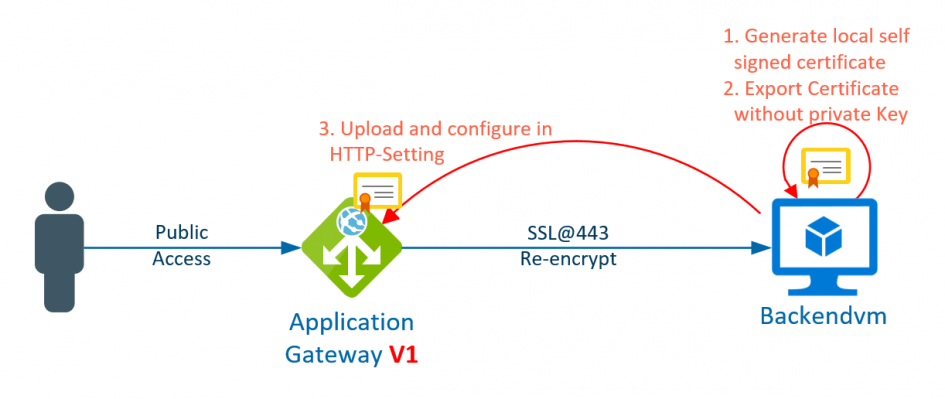
The Azure Application Gateway is a load balancer with some additional features, such as path-based routing, a web application firewall or SSL termination. However, if the traffic to the backend has to be encrypted also, (it has to be re-encrypted), this is also possible.
However, the setup of re-encrypt differs for version 1 and version 2 applications gateways. The process for version 1 is described in this post.
1. Generate SSL Certificate (here on Windows)
The first step is optional if the certificate is generated by a corresponding issuer. A self-signed certificate should serve as an example here. The creation is easy and goes directly in the IIS.
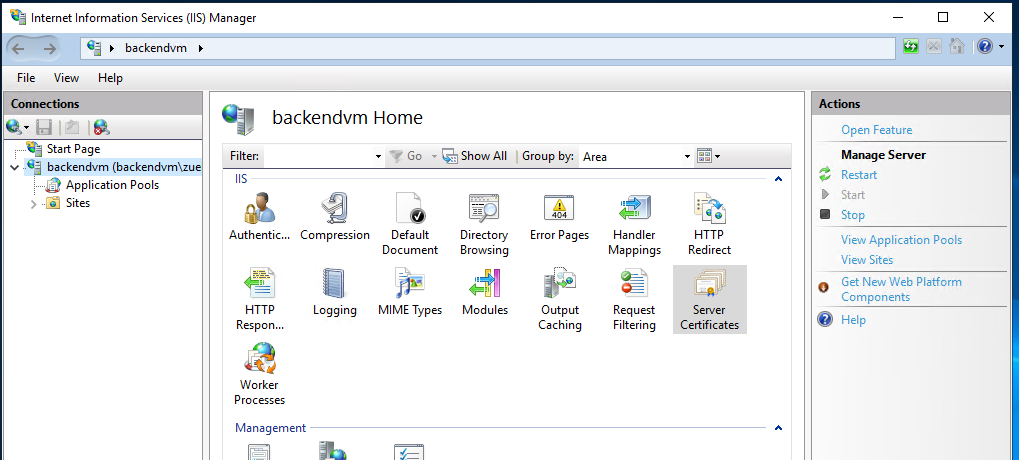
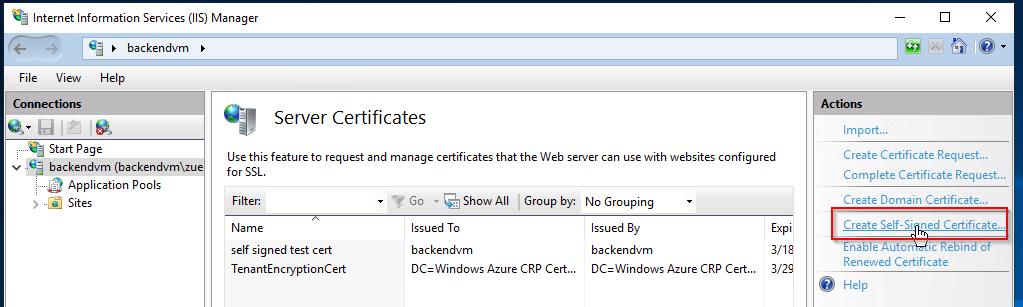
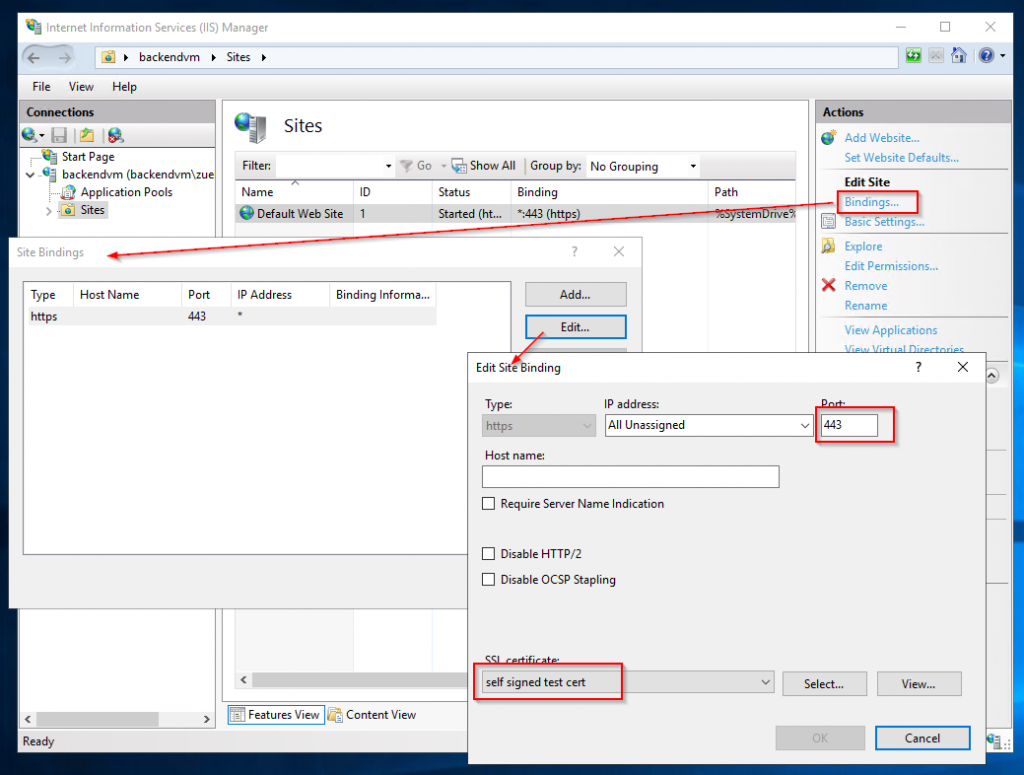
2. Export Certificate
The second step is to export the certificate. It is only important that the certificate is exported as Base-64 CER-file. The key does not have to be exported. Application gateway only needs the public key of the certificate. The process is simple in IIS:
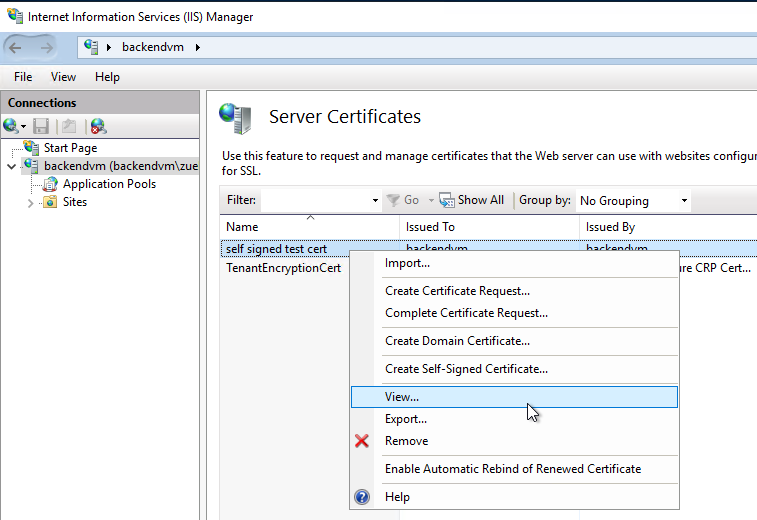


3. Configure Application Gateway with the exported Certificate
The last step is to configure the application gateway. In order to configure the backend re-encryption, the HTTP settings must be switched to HTTPS (Port 443) and the exported certificate must be uploaded. The name of the certificate is automatic changed to a unique internal name that begins with back-setting.
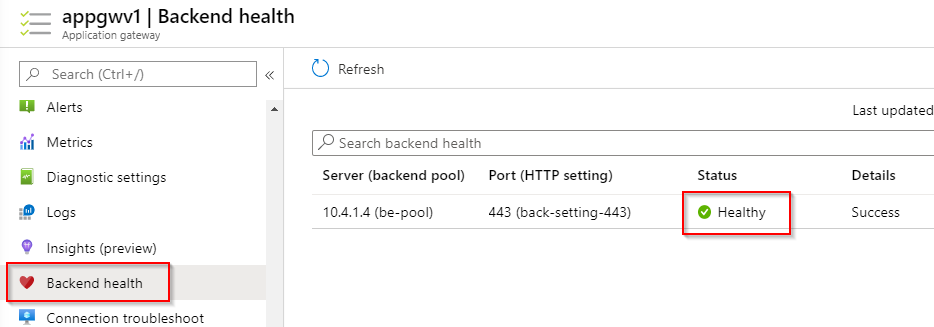
If the settings are correct and the backend is responding on port 443, it is displayed as healthy unter the blade backend health.

1 Pingback