Kategorie Security
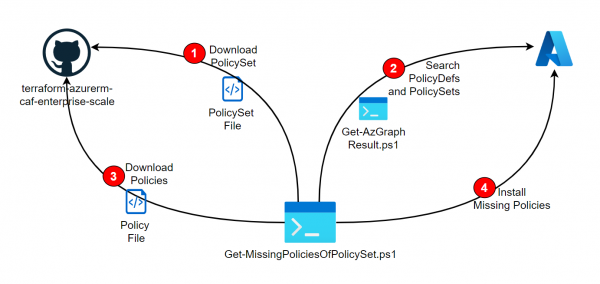
As described in the Post Deploy PolicySets from Azure Landing Zone Repository, PolicySets (Initiatives) can be installed directly from the Azure Landing Zone Repositiory. However, if these references other policies, they must already be installed beforehand. The following script is… Weiterlesen →
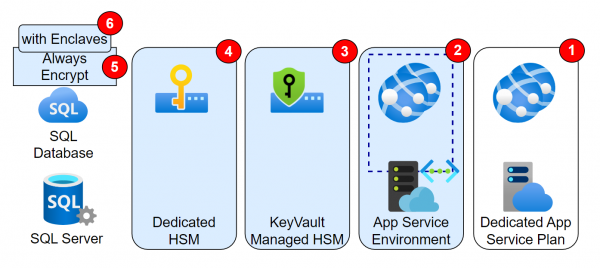
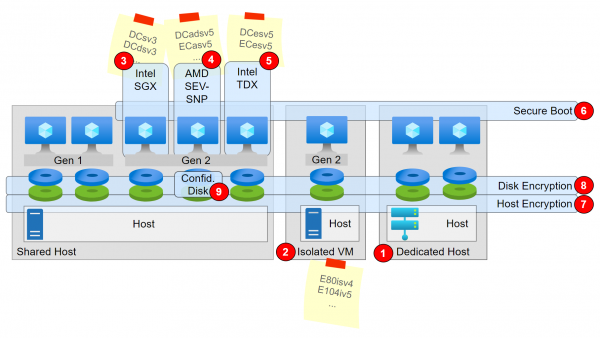
Introduction The previous article described the Confidential Computing features related to VMs. The same approach, i.e. securing data during processing, also applies to PaaS. These features will be discussed in this post. Features Featured not in the Picture
Introduction Microsoft refers to the CCC in its definition: The Confidential Computing Consortium defines confidential computing as: The protection of data in use by performing computations in a hardware-based Trusted Execution Environment (TEE). And describes the encryption of data-in-use in… Weiterlesen →
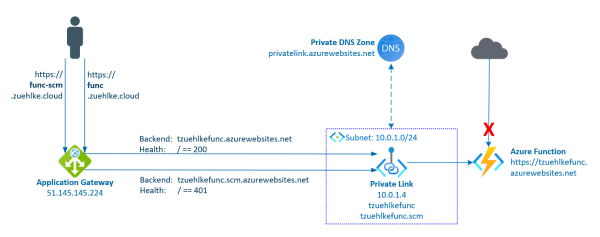
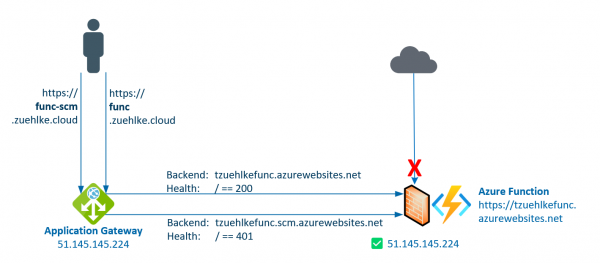
The previous post described how to deploy to an Azure Function if access is protected by an Application Gateway. Access to the function and to the management endpoint as well were protected. The Function was protected by the Function App… Weiterlesen →
Azure Functions are a serverless way to run code. They support different programming languages and can scale quickly. As a developer, it is particularly easy to deploy functions directly from Visual Studio or Visual Studio Code. Functions are often protected… Weiterlesen →
Most resources in Azure can be well protected by disabling public access. If public access is completely deactivated, access can take place via private endpoints. In most cases it is sufficient to restrict access to selected network to use service… Weiterlesen →
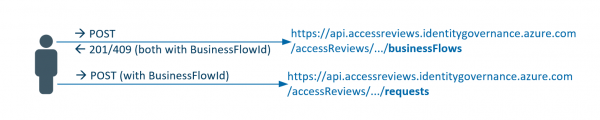
Azure resources (e.g. subscriptions) can be better protected with PIM. As a result, access roles are not granted permanently, but must be requested for a specified period of time. After this period, the permission is automatically revoked. If the PIM… Weiterlesen →
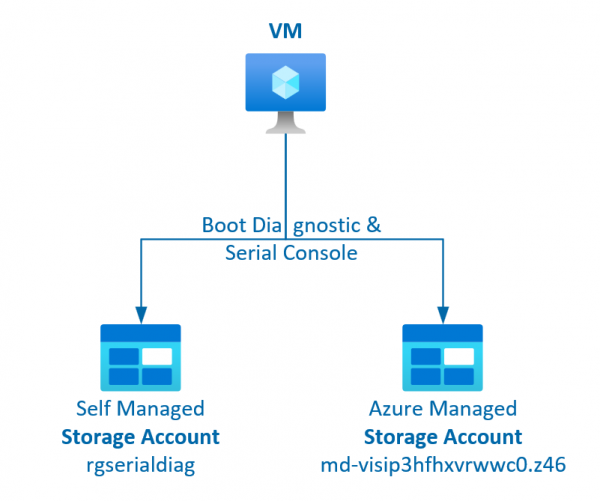
The serial console for VMs is a very useful tool for adapting the VM or making checks via the portal. For this, however, the boot diagnostics must be activated (i.e. a storage account for the logs must exist) and the… Weiterlesen →
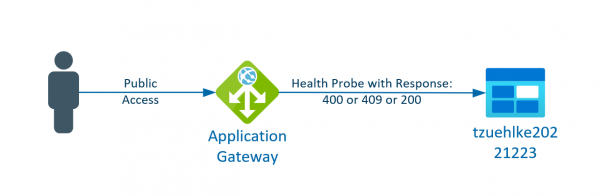
Storage accounts are also often used as backend pools for Application Gateway. This allows the storage to be protected with private endpoints or service endpoints and accessed via a central entry point with an alternative URL. However, the Application Gateway… Weiterlesen →
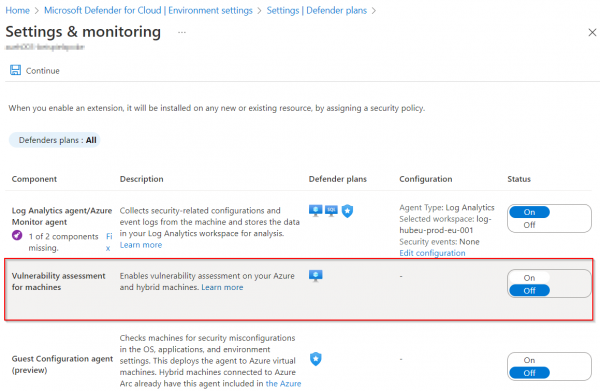
The Defender for Cloud offers are used to receive notifications and alerts about Azure Services. To do this, it can be activated per subscription and per Azure Service (e.g. with Set-AzSecurityPricing or in the portal). However, what is not supported… Weiterlesen →
I had problems with the instructions from my post, because Lets Encrypt is switching from ACME API v1 to ACME API v2. So I switched to acme.sh to generate Let’s Encrypt certificates in manual DNS mode. The steps are simple… Weiterlesen →
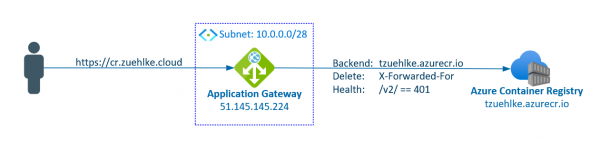
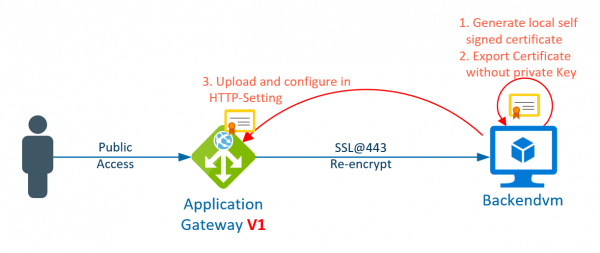
The Application Gateway v2 has considerable advantages over the v1. Support for autoscaling, zone redundant operation or use as an ingress in the AKS are just a few features from the list. The re-encryption of the back-end data traffic is… Weiterlesen →
The Azure Application Gateway is a load balancer with some additional features, such as path-based routing, a web application firewall or SSL termination. However, if the traffic to the backend has to be encrypted also, (it has to be re-encrypted),… Weiterlesen →