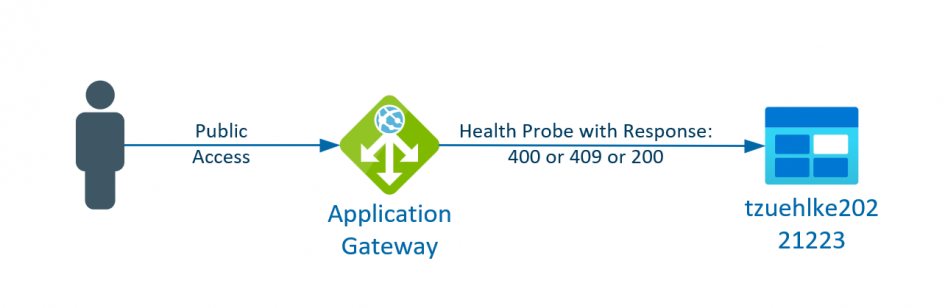
Storage accounts are also often used as backend pools for Application Gateway. This allows the storage to be protected with private endpoints or service endpoints and accessed via a central entry point with an alternative URL.
However, the Application Gateway constantly checks whether the backend pool can be reached. To do this, it regularly sends requests to the backend URL and expects responses with the HTTP status code between 200 and 399. However, there are various options for a storage account (depending on the configuration). The possibilities are shown below:
| Config | Test/URL (for health probe) | Result (to use in health probe) |
|---|---|---|
| – “Allow Blob public access” is enabled | curl -i -X GET -H “x-ms-date: $(date -u)” “https:// tzuehlke20221223.blob.core.windows.net/“ | 400 Value for one of the query parameters specified in the request URI is invalid. |
| – “Allow Blob public access” is enabled – anonym accessable container “ healthcheck” was created | curl -i -X GET -H “x-ms-date: $(date -u)” “https:// tzuehlke20221223.blob.core.windows.net/healthcheck/?comp=list“ | 200 OK |
| – “Allow Blob public access” is disabled | like line 1 | 409 Public access is not permitted on this storage account. |
| – “Allow Blob public access” is disabled – add SAS for list operation to query | curl -i -X GET -H “x-ms-date: $(date -u)” “https://tzuehlke20221223.blob.core.windows.net/?comp=list&sv=2021-06-08&ss=b&srt=s&sp=l&se=2025-12-23T22:54:01Z&st=2022-12-23T14:54:01Z&spr=https&sig=N38QjP%2BHmRDqC1TvvYRPJhqe47yi90i%2FMEFAAddl9IY%3D“ | 200 OK |
Config for Storage Account with Public Access but no anonymous access
The storage account can be accessed publicly if Allow Blob public access is enabled in the configuration. This setting allows anonymous access to blobs if the containers are created for anonymous access.
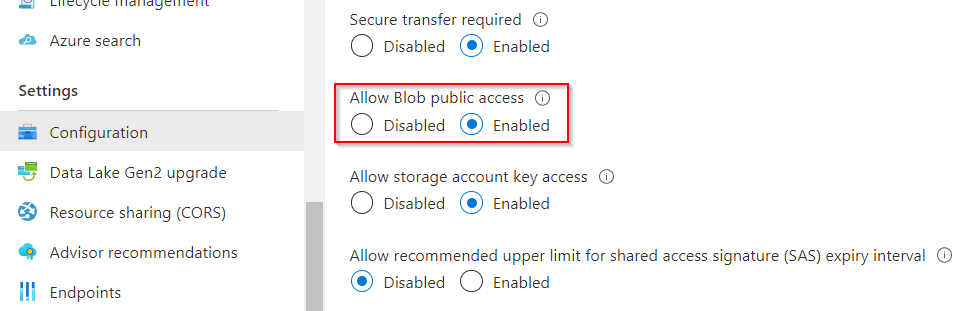
If this property is active, the storage account throws a 400 error if it is accessed at the root:
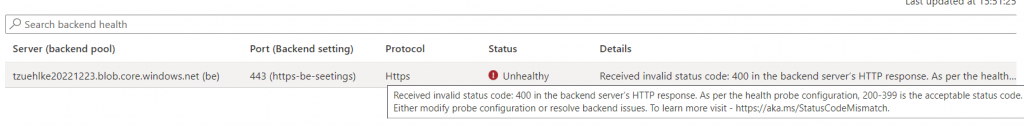
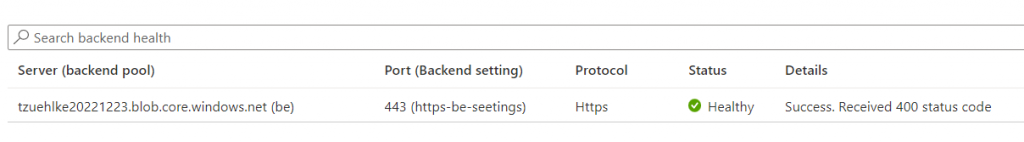
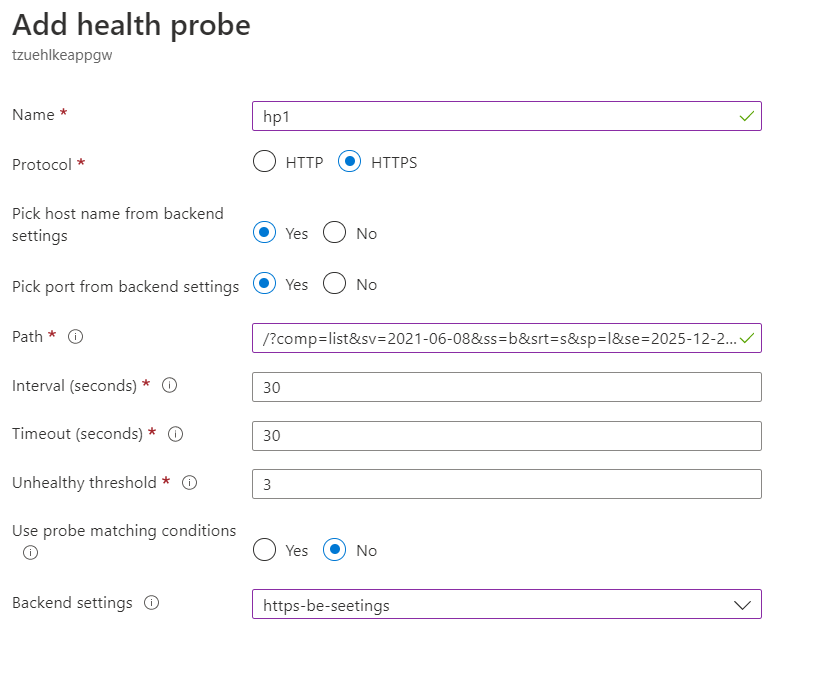
But in the application gateway, the expected response value of the health probe can now be set to 400, because the service is available and that should be ensured by the health probe:
Config for Storage Account with Public Access and anonymous access
To use anonymous access, a container for anonymous access must be created:

No data should be stored in this container because it would be public accessible without authentication. But it can be used to request a listing and get a 200 response:

Config for Storage Account without Public Access and without authentication
If public access is deactivated, the root URL can be accessed directly again. In this case, however, the answer is the error code 409.
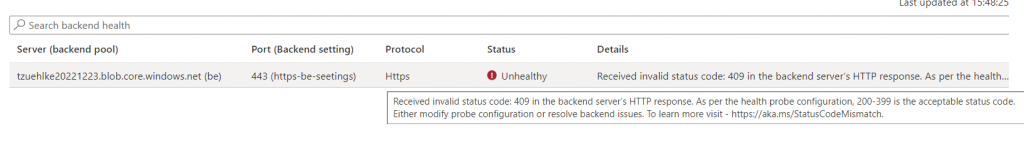
This error code could be used at the health probe to integrate the backend successfully.
Config for Storage Account without Public Access and SAS
The easiest way to get real access to a storage account without actually retrieving data is to list its contents. The List permission, which can be granted by a SAS token, is sufficient for this:
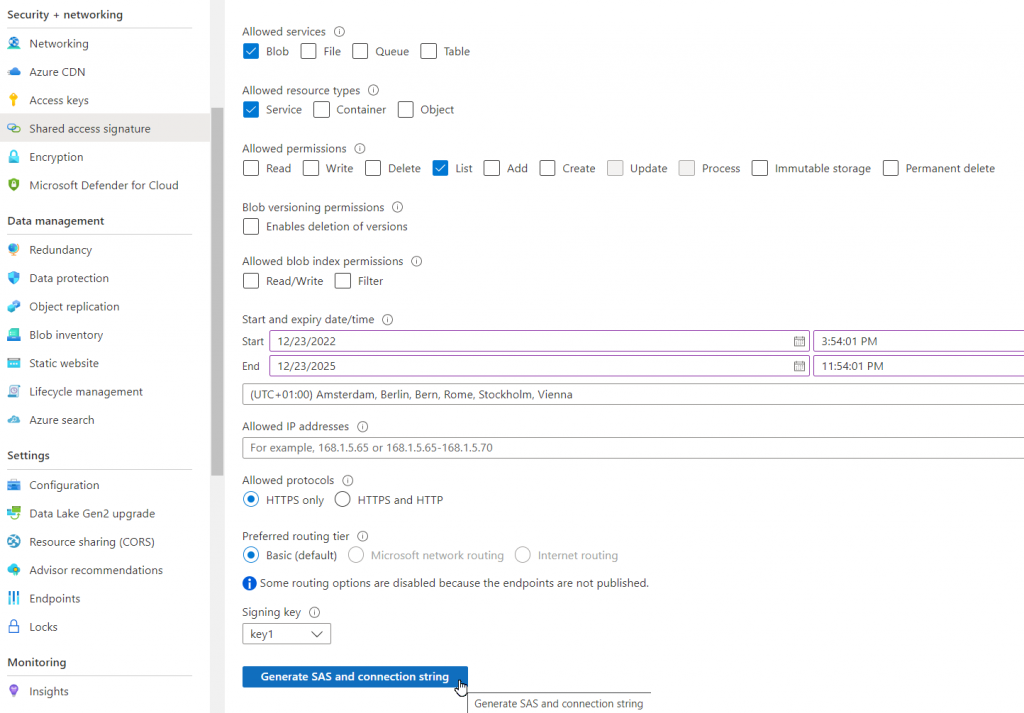
The probe can now accessed the storage account with the list command (comp=list) and the SAS token (sv=2021-06-08&ss=b...):
Using Managed Identity of the Application Gateway is not possible
It is possible to assign a managed Identity to an Application Gateway with the command Set-AzApplicationGatewayIdentity. But the probes do not use this Identity and they can therefore not be used to authenticate against a storage account.
Schreibe einen Kommentar