Kategorie Azure
If existing environments are recreated in Terraform, the resources already exist. Therefore, the resources must be transferred to the Statefile for management by Terraform. The output for a Terraform apply is: already exists – to be managed via Terraform this… Weiterlesen →
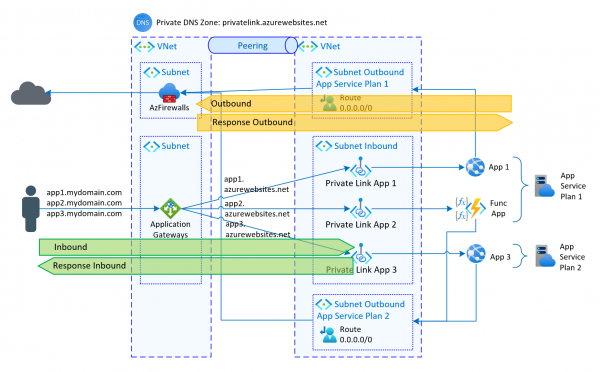
The Azure Application Gateway supports various routing options. With path-based routing, one or the other backend can be called depending on the URL. Things get a little more complicated when the apps on the app services are distributed in virtual… Weiterlesen →
The European Cloud Summit took place in Wiesbaden from May 14th to 16th. 3,000 participants and over 200 speakers met in the RheinMain CongressCenter. The sessions at the Cloud Summit were structured into 5 different tracks: Business and Strategy, Open… Weiterlesen →
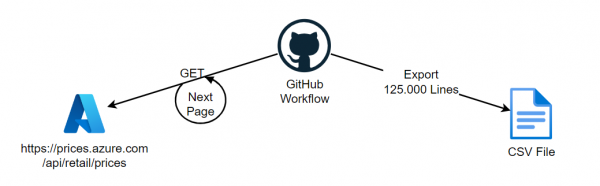
Idea A repository will be created in which the price history of Azure can be tracked. Since the API for pay-as-you-go prices does not provide historical data, a repository with past prices should be created as CSV files. These files… Weiterlesen →
If the software and inventory functionality is only used for the supported regions, the new approach can be used via the AMA and the documentation can be followed, which unfortunately contains some errors. From August, the new way via AMA… Weiterlesen →
In order to use the software inventory and change tracking, regardless of the region, the deprecated Microsoft Monitoring Agent must currently be used. The solution uses an Azure Automation account that is connected to the MMA/OMS Extension and reports the… Weiterlesen →
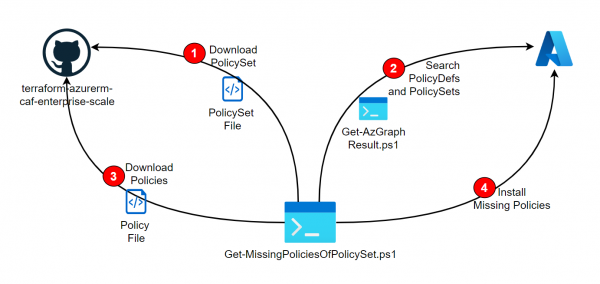
As described in the Post Deploy PolicySets from Azure Landing Zone Repository, PolicySets (Initiatives) can be installed directly from the Azure Landing Zone Repositiory. However, if these references other policies, they must already be installed beforehand. The following script is… Weiterlesen →
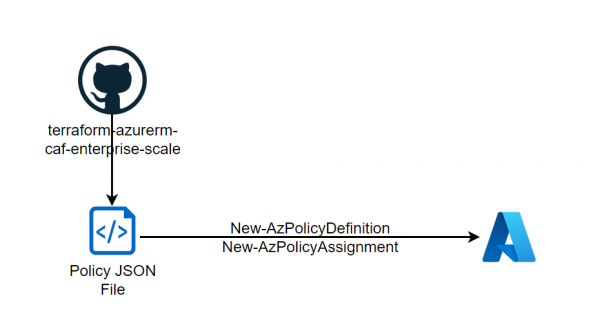
As described in the previous post, policies can be downloaded from the Enterprise Scale Architecture Repository and deployed into your own tenant. In addition to the mentioned policies, the repo also provides interesting Policy Initiatives (Policy Sets) that can also… Weiterlesen →
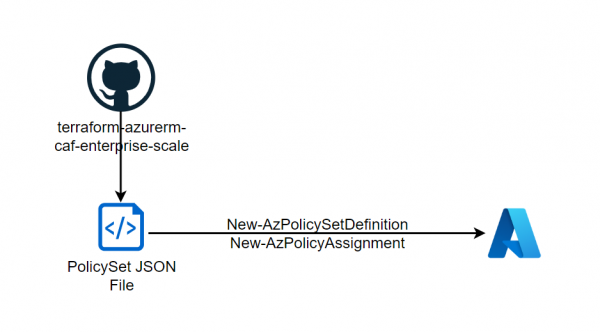
With the Enterprise Scale Architecture, Microsoft offers various landing zone designs that can be used directly as Terraform or Bicep. Interesting is that the repository also contains policies that are not available in the Azure portal. Microsoft recommends these policies… Weiterlesen →
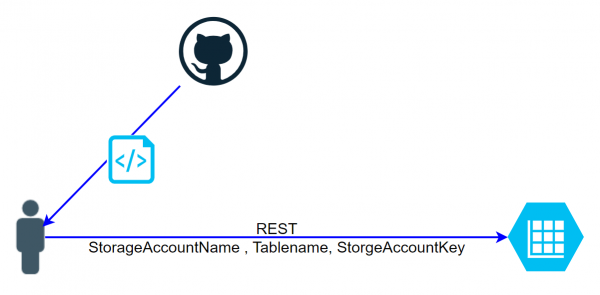
There are various ways to access a table of a storage account. If the storage account key is used, the request for the REST call must be generated in a complicated manner. The script getaztablerows.sh on Github shows the calculation:… Weiterlesen →
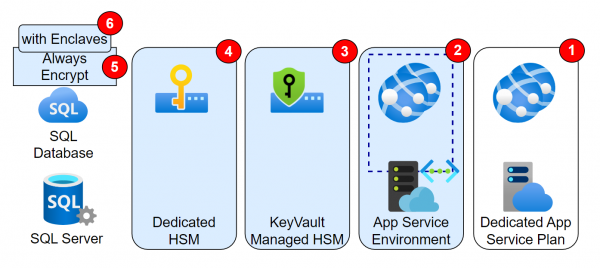
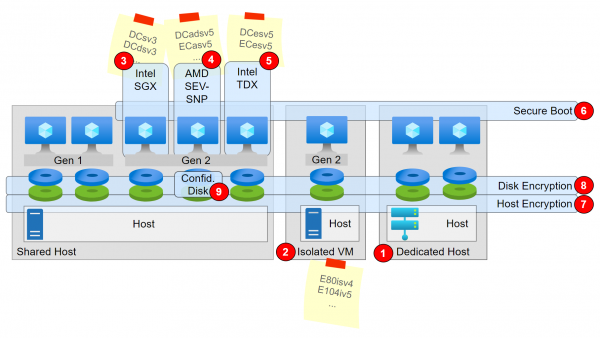
Introduction The previous article described the Confidential Computing features related to VMs. The same approach, i.e. securing data during processing, also applies to PaaS. These features will be discussed in this post. Features Featured not in the Picture
Introduction Microsoft refers to the CCC in its definition: The Confidential Computing Consortium defines confidential computing as: The protection of data in use by performing computations in a hardware-based Trusted Execution Environment (TEE). And describes the encryption of data-in-use in… Weiterlesen →
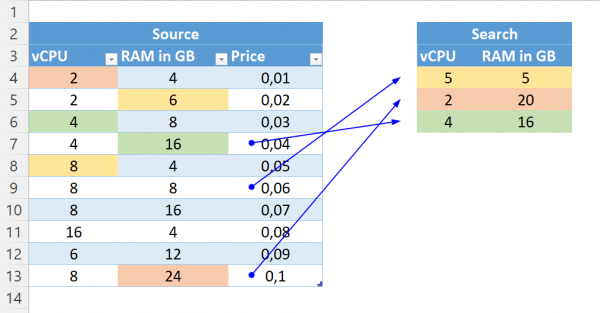
The Problem For OnPrem VMs, with specific vCPU and RAM, the right VM sizes often have to be found in Azure. It is important that the prices are as low as possible. For example, with Windows, a machine with 8… Weiterlesen →
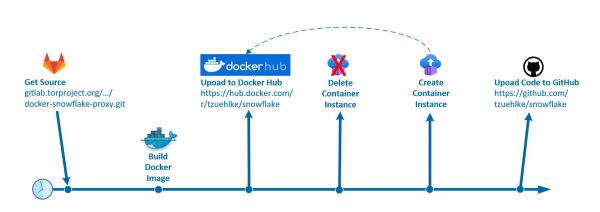
What is snowflake? “Snowflake is a system that allows people from all over the world to access censored websites and applications. Similar to how VPNs assist users in getting around Internet censorship, Snowflake helps you avoid being noticed by Internet… Weiterlesen →
Cloud governance plays a very important role in the adaptation of the cloud. Cloud governance defines the guidelines for the cloud, i.e. the restrictions that should apply in the cloud, but also the freedom that every user can have. The… Weiterlesen →
Bei der Adaption der Cloud spielt die Cloud Governance eine ganz wesentliche Rolle. Die Cloud Governance definiert die Richtlinien für die Cloud, also die Einschränkungen, die in der Cloud gelten sollen, aber auch die Freiheiten, die jeder User haben kann…. Weiterlesen →
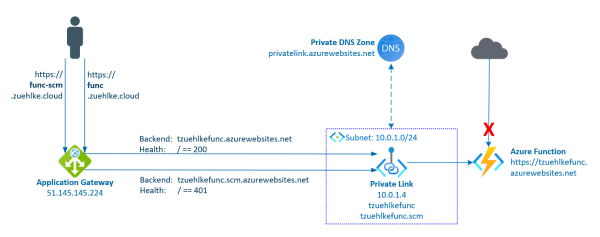
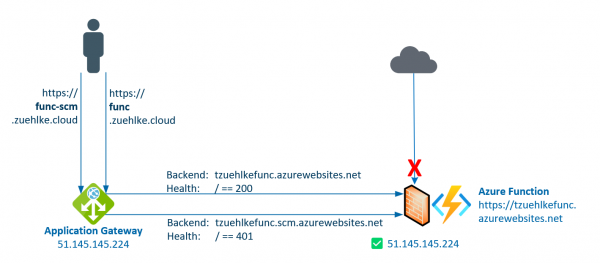
The previous post described how to deploy to an Azure Function if access is protected by an Application Gateway. Access to the function and to the management endpoint as well were protected. The Function was protected by the Function App… Weiterlesen →
Azure Functions are a serverless way to run code. They support different programming languages and can scale quickly. As a developer, it is particularly easy to deploy functions directly from Visual Studio or Visual Studio Code. Functions are often protected… Weiterlesen →
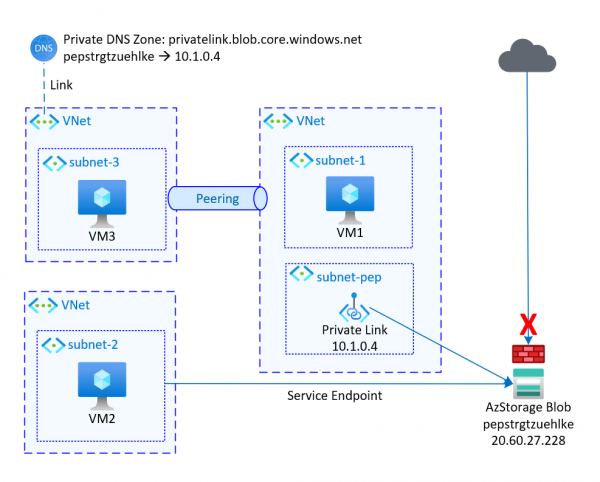
Most resources in Azure can be well protected by disabling public access. If public access is completely deactivated, access can take place via private endpoints. In most cases it is sufficient to restrict access to selected network to use service… Weiterlesen →
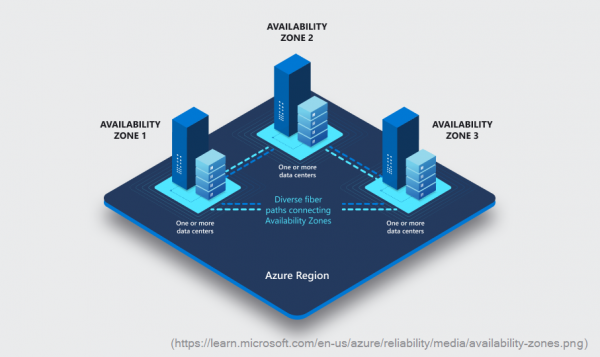
The concept of Availability Zones is well explained in the Microsoft documentation. These are different physical locations within a region that have separate power, cooling, and network infrastructure. When building a resource, it can often be decided in which Availability… Weiterlesen →
Azure resources (e.g. subscriptions) can be better protected with PIM. As a result, access roles are not granted permanently, but must be requested for a specified period of time. After this period, the permission is automatically revoked. If the PIM… Weiterlesen →
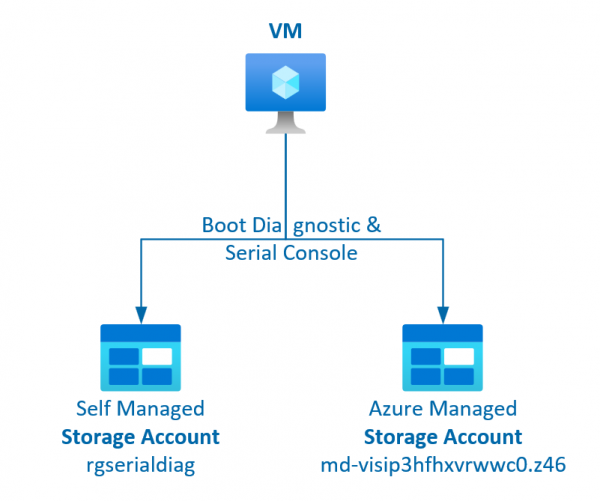
The serial console for VMs is a very useful tool for adapting the VM or making checks via the portal. For this, however, the boot diagnostics must be activated (i.e. a storage account for the logs must exist) and the… Weiterlesen →
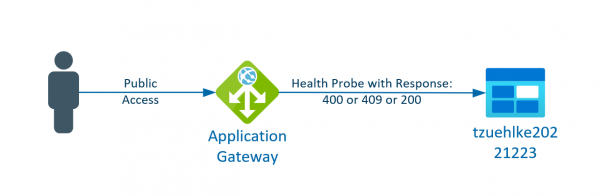
If an AppService is called directly via its IP, either the certificate is invalid or the page cannot be found. If the call is made via HTTPS, the automatic generated certificate only stores the DNS name and not the IP,… Weiterlesen →
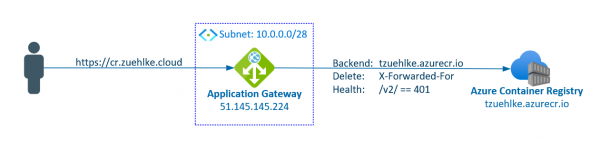
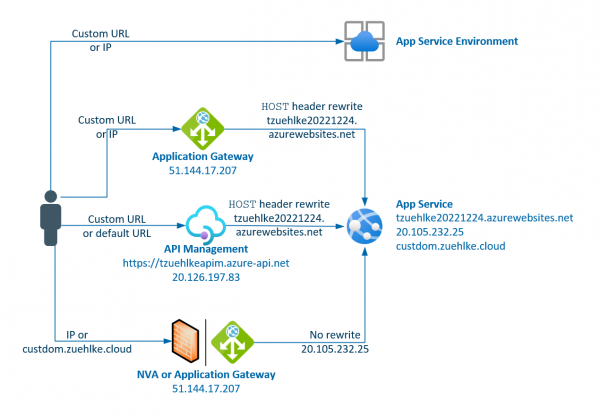
Storage accounts are also often used as backend pools for Application Gateway. This allows the storage to be protected with private endpoints or service endpoints and accessed via a central entry point with an alternative URL. However, the Application Gateway… Weiterlesen →
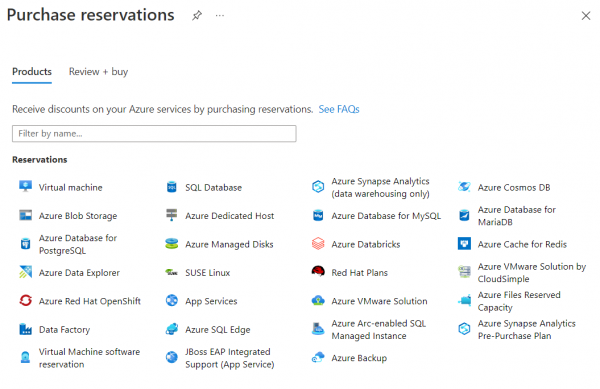
Various resources can be reserved in Azure, whereby use is guaranteed for 1 or 3 years. This can reduce the price of these resources by up to 72%. In the portal you can see these reduced costs for the reservations:… Weiterlesen →
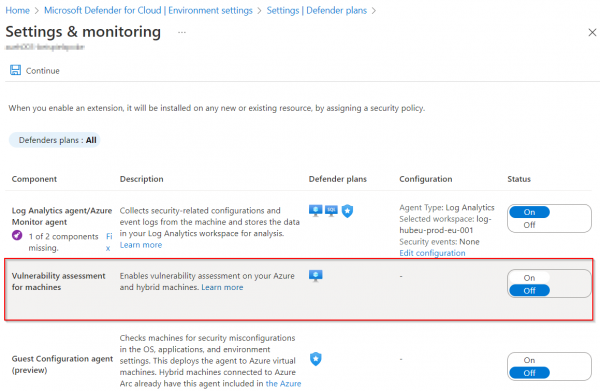
The Defender for Cloud offers are used to receive notifications and alerts about Azure Services. To do this, it can be activated per subscription and per Azure Service (e.g. with Set-AzSecurityPricing or in the portal). However, what is not supported… Weiterlesen →
To set up a budget with warning in Azure, the Az.Billing PowerShell Module offers the cmdlets New-AzConsumptionBudget. Unfortunately, the PowerShell commands don’t seem to be implemented correctly in version 2.0.0 at the Az Module 8.3.0 or newer (currently 9.0.1): The… Weiterlesen →
As described in the previous article, private endpoints can be used to securely access Azure services. With App Services there is an additional possibility to control the outgoing traffic. Specifically, when configuring the app service in the network area, 2… Weiterlesen →
Most Azure services are accessible via a public URL. However, to provide a higher level of protection and a direct connection, various options are available in Azure. The two most common approaches are Service Endpoints and Private Endpoint/Private Link. Service… Weiterlesen →
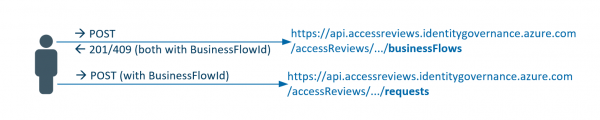
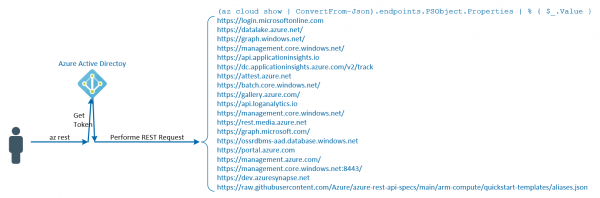
APIs are available for most functionality and information in Azure. A token, which must be sent with the request, is usually required to retrieve the information. Generating a token dynamically or retrieving it via a service principal is often a… Weiterlesen →