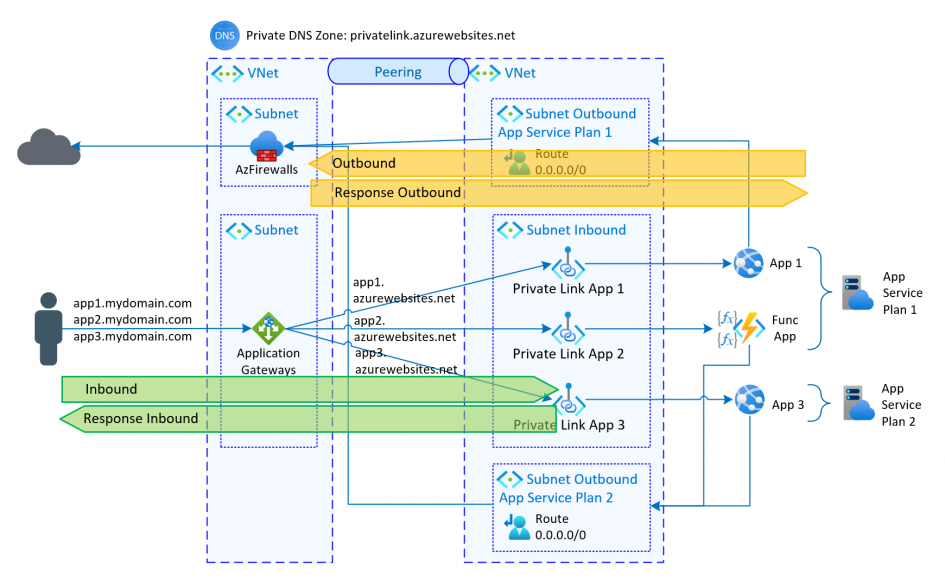
As described in the previous article, private endpoints can be used to securely access Azure services. With App Services there is an additional possibility to control the outgoing traffic. Specifically, when configuring the app service in the network area, 2 settings are available:
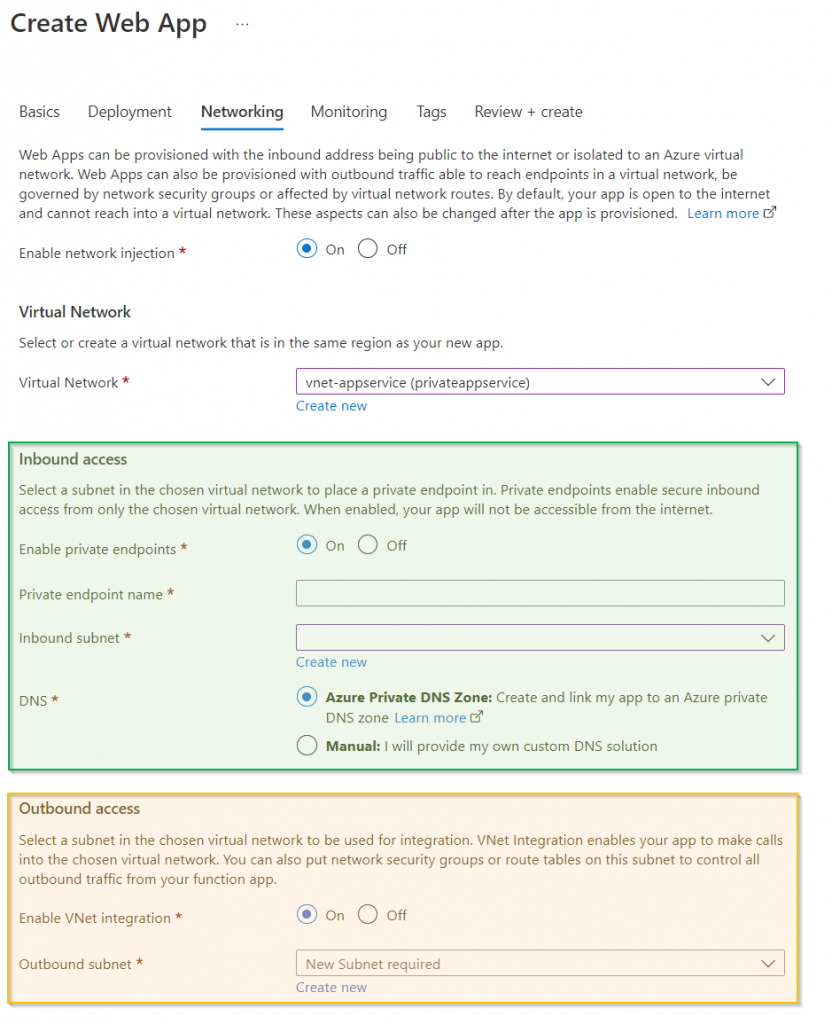
Inbound access
The first setting controls external access to the App Service. A subnet can be selected from which an IP is selected for the private endpoint. This subnet can be used by different types of services for their private endpoints.
By assigning the private endpoint, access can only take place via the new internal IP of the endpoint. Public access is prohibited and direct access to the website generates a 403 response.
If an app service is called via the private endpoint, the response is also made via the private endpoint. In the example, access is controlled via an Application Gateway, which forwards the call to the app service and sends the app service’s response back to the caller.
Currently there is a preview feature for Access Restriction. This feature can also be used to activate additional public access:
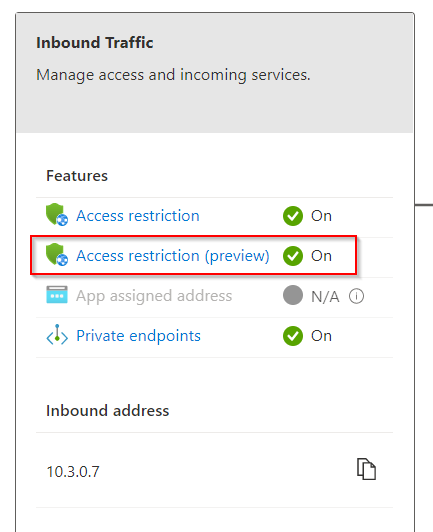
Outbound access
In contrast to other Azure services, App Services can also set up outgoing connections themselves. This can be done, for example, by Timer Triggered Functions.
Normally, outgoing communication goes directly to the Internet. The answer follows the same path (directly from the Internet and past the private endpoint). An outbound configuration can be used to redirect the outgoing connection. Each function app (with all its functions) and each app service can have its own VNet integration and thus outbound configuration.
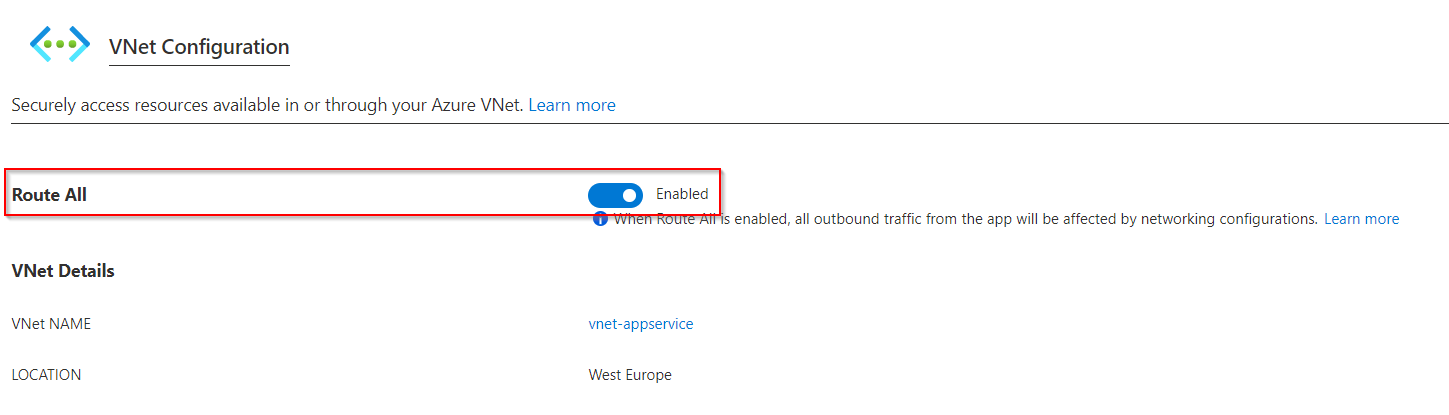
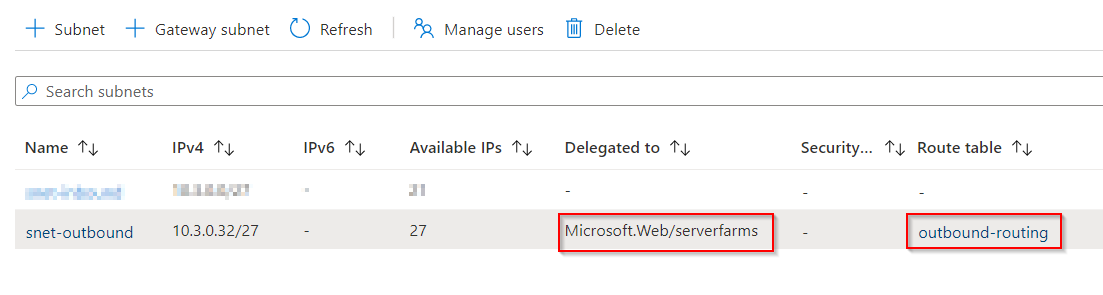
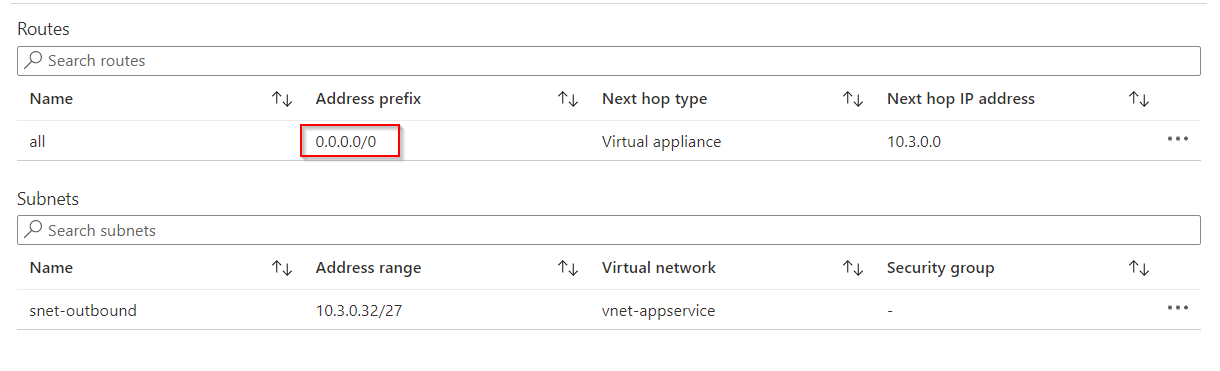
To redirect all outbound traffic, a VNet integration must be done, with all traffic being redirected (Route All). In addition, the integrated subnet needs to route all traffic (0.0.0.0/0) to a specified next hop (e.g. the firewall). The integrated subnet can only be used for the same types of services, since they can only be assigned to exactly one service type (Delegated to).
Schreibe einen Kommentar