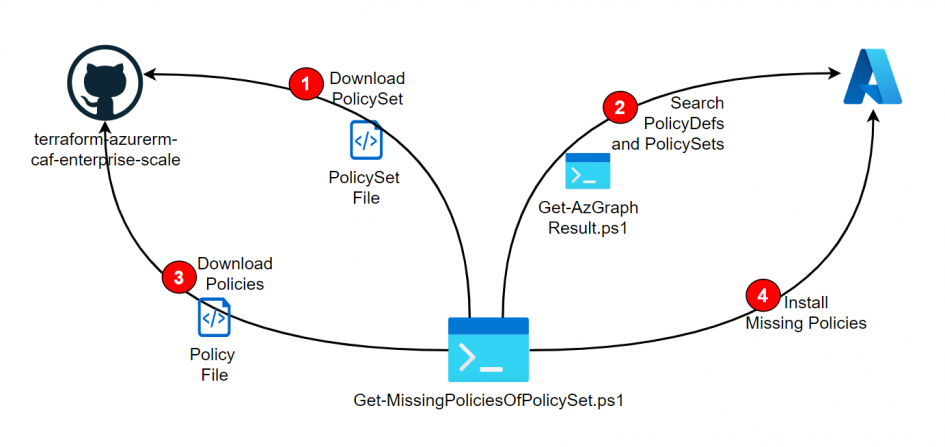
As described in the Post Deploy PolicySets from Azure Landing Zone Repository, PolicySets (Initiatives) can be installed directly from the Azure Landing Zone Repositiory. However, if these references other policies, they must already be installed beforehand. The following script is used to carry out this check and install the missing policies from the Azure Landing Zone repo.
The Get-MissingPoliciesOfPolicySet.ps1 script downloads the initiative in lines 10 and 11 (it is passed as a parameter) and determines the referenced policies in line 12. In addition, the path of the policy definitions is cleaned up in line 12.
In line 16, the script Get-AzGraphResult.ps1 is used to determine all installed policies and policy sets. It is using the KQL policyresources | where type == "microsoft.authorization/policydefinitions" or type == "microsoft.authorization/policysetdefinitions". Only the IDs of the installed policies/policy sets are required. ⚠️ Keep in mind, that the script requires the installation of the Az.ResourceGraph module.
In line 20, the comparison is made based on the IDs as to which policies are still missing. If all policies are available, the script is terminated (line 23).
Afterwards, the missing policies are downloaded. All URLs of the landing zone repo that contain policy definitions are first determined in lines 27 to 29. They are then downloaded in lines 31 to 41 and if the policy is missing (line 36), it is installed (line 38).
[CmdletBinding()]
param (
[parameter(Mandatory = $true)]
[ValidateNotNullOrEmpty()]
[String]
$PolicySetJsonUrl
)
Write-Host "Getting PolicySet..."
$set = Invoke-WebRequest $PolicySetJsonUrl
$jsonset = $set.Content | ConvertFrom-Json -Depth 20
$neededPolicies = $jsonset.properties.policyDefinitions.policyDefinitionId.Replace('${root_scope_resource_id}', '')
Write-Host "Found $($neededPolicies.Count) Policies in PolicySet"
Write-Host -NoNewline "Determine installed Policies in Tenant and Subscriptions..."
$installedPolicies = ./Get-AzGraphResult.ps1 -Query 'policyresources | where type == "microsoft.authorization/policydefinitions" or type == "microsoft.authorization/policysetdefinitions"'
$installedPolicies = $installedPolicies.id
Write-Host "$($installedPolicies.Count)"
$missingPolicies = $neededPolicies | ?{-not ($installedPolicies -match $_)}
Write-Host "Found $($missingPolicies.Count) not installed Policies that are needed in PolicySet"
if($missingPolicies.Count -eq 0){
exit
}
Write-Host "Downloading missing Policies from GitHub..."
$gitresp = Invoke-WebRequest https://api.github.com/repos/Azure/terraform-azurerm-caf-enterprise-scale/git/trees/main?recursive=1
$gitfiles = ($gitresp.Content | ConvertFrom-Json -Depth 20).tree
$gitpolicies = $gitfiles | ? {$_.path.contains("/lib/policy_definitions/")}
$gitpolicies | % {
$url = $_.path
$resp = Invoke-WebRequest "https://raw.githubusercontent.com/Azure/terraform-azurerm-caf-enterprise-scale/main/$url"
$plcy = $resp.Content
$plcyObj = $plcy | ConvertFrom-Json -Depth 20
Write-Host "$($plcyObj.Name)..." -ForegroundColor Gray -NoNewline
if($missingPolicies -match $plcyObj.Name){
Write-Host -ForegroundColor Green "INSTALLING"
$plcyDef = New-AzPolicyDefinition -Name ($plcy | ConvertFrom-Json).Name -Policy $plcy
}else{
Write-Host -ForegroundColor Yellow "SKIP"
}
}
Below you can see an example run with corresponding output:
.\Get-MissingPoliciesOfPolicySet.ps1 -PolicySetJsonUrl https://raw.githubusercontent.com/Azure/terraform-azurerm-caf-enterprise-scale/main/modules/archetypes/lib/policy_set_definitions/policy_set_definition_es_deploy_diagnostics_loganalytics.tmpl.json Getting PolicySet... Found 70 Policies in PolicySet Determine installed Policies in Tenant and Subscriptions...3158 Found 53 not installed Policies that are needed in PolicySet Downloading missing Policies from GitHub... Append-AppService-httpsonly...SKIP Append-AppService-latestTLS...SKIP Append-KV-SoftDelete...SKIP ... Deploy-DDoSProtection...SKIP Deploy-Diagnostics-AA...INSTALLING Deploy-Diagnostics-ACI...INSTALLING Deploy-Diagnostics-ACR...INSTALLING Deploy-Diagnostics-AnalysisService...INSTALLING ... Deploy-Diagnostics-WVDHostPools...INSTALLING Deploy-Diagnostics-WVDWorkspace...INSTALLING Deploy-FirewallPolicy...SKIP ... Deploy-Windows-DomainJoin...SKIP
If the script is run a second time, all missing policies should already be installed and it should exit immediately. The original PolicySet can then be installed.
Schreibe einen Kommentar