Introduction
Microsoft refers to the CCC in its definition:
The Confidential Computing Consortium defines confidential computing as: The protection of data in use by performing computations in a hardware-based Trusted Execution Environment (TEE).
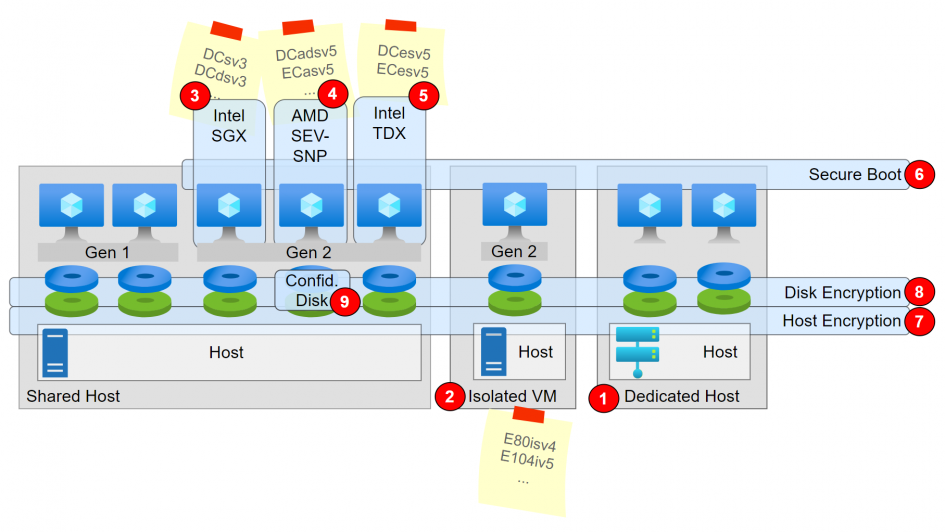
And describes the encryption of data-in-use in RAM & CPU. The basic idea is to protect the data from unauthorized access while it is being processed in the shared host system. But there are also other protective mechanisms that can also be counted as confidential computing, since they protect the data from unauthorized access. These mechanisms are shown in the picture and numbered accordingly.
Features
- Dedicated Hosts
- host for one customer only (no other customers)
- Dedicated hosts usually have many vCPUs (starts with 8 cores/8 vCPU up to 224 cores/416vCPUs)
- any VMs can be created on this host
- Isolated VM
- Custom VM running on exactly one host (which is therefore dedicated for one customer).
- usually very large VMs (because a whole blade is used), e.g. E80i… = 80vCPU
- in the azure SKU VM naming the “i” stands for isolated
- VM with Intel SGX
- SGX means Software Guard Extention
- Data can be held and processed in enclaves (enclave = RAM part + CPU part)
- Enclave are hardware encrypted
- Hypervisor, OS, users, apps and services cannot access the corresponding data and code running inside the enclave
- Data outside of Enclave is not encrypted
- is only used with VMs of type DCsv2, DCsv3, DCdsv3 (the “C” in the SKU VM naming stands for confidential
- these VMs can (with additional configuration) also be used as Kubernetes worker nodes to get confidential containers
- Client application must be adapted and must use the DCAP library to use the enclaves
- only makes sense for self-created software
- VM with AMD SEV-SNP
- SEV-SNP means Secure Encrypted Virtualization – Secure Nested Paging
- Entire VM is encrypted, thereby preventing access for: Hypervisor and host administrator and also the Cloud Service Provider (Microsoft)
- the data is not encrypted for other applications, services on the same machine
- supported VM series: DCasv5, DCadsv5, ECasv5, ECadsv5 (the “C” in the SKU VM naming stands for confidential and the “a” stands for AMD)
- the VMs can also be used directly (without configuration) as a node pool for AKS
- can be used to create directly a confidential container instance
- is the only option with purchased software
- VM with Intel TDX (private Preview)
- TDX means Trusted Domain Extentions
- Intel TDX helps harden the virtualized environment to deny the hypervisor and other host management code access to VM memory and state, protecting against operator access.
- supported VM series: DCesv5, ECesv5
- you need to sign up for the preview
- Secure Boot
- is part of Trusted Launch
- is possible for all Generation 2 VMs
- each step in the boot process checks a cryptographic signature of the subsequent steps
- prevents for rootkits and malicious operating systems and malicious software packages
- Encryption at host
- encrypts the path from storage to CPU
- encrypts all data storage (regular disks again, temp hard disk, cache, …)
- cannot be used simultaneously with Disk Encryption (DM-Crypt/Bitlocker)
- Azure Disk Encryption (ADE)
- can be used for OS disk and data disk
- windows OS using BitLocker
- linux OS using DM-Crypt
- must be configured and activated via CLI or PowerShell (not via portal)
- key is stored in KeyVault
- Confidential Disk Encryption
- works with OS Disk only
- binds the Disk Encryption Key to the vTPM of the VM, therefore the VM only can read/write the disk
- PMK or CMK can be used
- can only be used with DCa VMs (with AMD SEV-SNP).
Features not in Picture
The follwoing two features are missing in the picture because they are activated by default or are extensions to the features mentioned above:
- Encryption-At-Rest = Default Storage Encryption = is always enabled and cannot be prevented
- Double-Encryption-At-Rest = double encryption of the regular activated standard encryption for managed data disks (this requires the encryption set to be created in KeyVault and assigned it to the disk)
1 Pingback